
By Ari SInger, CTO
and Ives Brant, Director of Marketing
TPMs (trusted platform modules) were the first broadly adopted commercial technology specifically designed to answer a fundamental question of trusted computing, “Is this device compromised?” It’s a critical point, given that nation-states and [very] organized crime will focus intensely on compromising IoT (Internet of Things) endpoints, from security cameras to control (SCADA and/or DER) systems and smart meters for the energy sector, not to mention the ubiquitous video doorbells.
Authenta flash memory: attestation and secure boot
Now Micron, a leading technology company, has answered the “Are we compromised?” question with its next-generation security product, Authenta. A security technology integrated into a flash memory chip, creating what is essentially a two-in-one device, Authenta achieves this through a security capability called attestation. Authenta includes other important functions, such as those that support secure boot. At TrustiPhi, we believe that attestation is crucial for many IoT endpoints, and provides opportunities for competitive advantage to manufacturers and operators of such devices.
Threats that Authenta Addresses
“A security gap exists at the lowest levels of boot in many systems where discrete flash memory components store system-critical code and data.
The flash has become the target for many hackers to create Advanced Persistent Threats (APT’s) that can mask themselves from higher levels of code and resist removal. In many of these cases, flash memory is re-imaged or rewritten with new malicious code undermining the integrity of that device.
Micron Authenta™ technology integrates true hardware-based roots of trust into flash memory, enabling strong cryptographic identity and health management for IoT devices. By moving essential security primitives in-memory, it becomes simpler to protect the integrity of code and data housed within the memory itself.” Source: www.micron.com
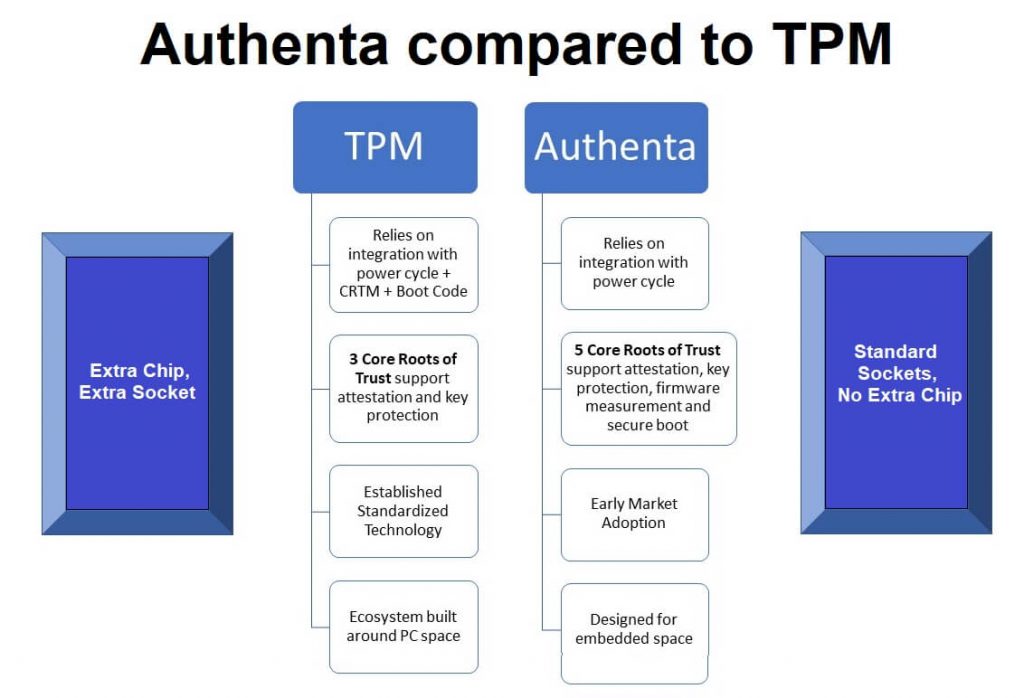
PCs are not the same as IoT endpoint products
TPM has been a de facto standard in PCs for many years, while Authenta is a relative newcomer. However, having played a key role in the development and deployment of both TPMs and Authenta [during its development] for years, TrustiPhi engineering teams see some key advantages for Authenta in future IoT endpoint products.
Other hardware security choices will be available to makers of endpoint products, but we expect Micron’s market position will motivate them to give Authenta a close look – and they will like what they find.
Are we saying that TPM’s day is over?
Not at all. The TPM has shown tremendous utility over the years in system security, particularly for PCs — and it has considerable potential for the IoT market in specific scenarios. However, as experienced engineers who build security into system architectures and have designed TPM-based solutions, we view Authenta as more attractive than TPMs for most IoT deployments.
Why is Authenta better for Internet of Things endpoints?
Let’s start with something practical: TPMs are VERY HARD. Authenta is EASIER. Our team includes architects who helped create the TPM 2.0 standard. Tech companies with deep resources hire us to “do TPM” for them. We know TPMs inside and out. They are extremely complex to integrate and deploy – although once deployed, they are fairly manageable.
With Authenta, engineers need skills and knowledge, but the combined flash + security hardware is much more straightforward, in most cases, to integrate into a system. Therefore, Authenta is faster and less costly when it comes to skilled engineering time and your product timetable. Use Authenta once, and subsequent incorporation into additional products is comparatively simple.
Manufacturers like Authenta’s cost economies and feature set, and many have or are considering integrating it into their product lines. That said, Authenta is relatively new and not yet widely adopted and propagated. The market is also waiting for Micron and its partners to build simple interfaces and platforms to make it easy to manage Authenta-based devices. This will strengthen Authenta’s IoT market advantage.
A big plus: Authenta fits into a standard flash memory socket
Authenta requires no special socket on a circuit board – in contrast to TPMs, which may require significant board rework. No board or SoC (System on a Chip) changes are needed to use Authenta. It uses standard interfaces such as SPI or eMMC.
Authenta co-locates the security mechanisms with the data assets in one chip
Authenta is a memory chip that integrates crypto functions and key storage inside a security perimeter along with the asset to be protected. It reduces the requirement for protecting the flash memory with a secure element located in or alongside the SoC.
Authenta also incorporates the Trusted Computing Group’s Device Identifier Composition Engine (DICE) along with storage protection. These are useful features that we will address in another blog.
Architecting a TPM-based security architecture is not for beginners
The complexities of TPMs present thorny product development issues for manufacturers. TPM functions are well established, but most engineers will not know the best ways to leverage them. Using TPMs in the IoT space is complicated and relatively costly. With Authenta, on the other hand, if the IoT device uses built-in flash memory, product development takes a big jump ahead. For these reasons, Authenta has a greater chance of being widely used in IoT endpoints.
What’s the problem in using TPM for billions of IoT devices, if it worked well in PCs?
There’s nothing wrong with using TPM if you know how to do it and can architect it into your product. But, when companies build IoT devices, they want the easiest path to a market-ready product, and they seek to grind every molecule of cost factor out of their designs. If there’s a less-expensive alternative, they’ll probably choose it over TPM.
“Device attestation is a valuable capability,
and in many cases is required for IoT endpoints.
Merely identifying the device is no longer sufficient.
Any security product should do that,
but attestation can be a product differentiator.”
Andy VanDamia
VP of Product Development, TrustiPhi
Most TPMs are hardware-based (although firmware-based TPMs are used in some products), and hardware TPMs require an extra chip in a system, which causes a noticeable cost jump in any IoT device with a low price point. Authenta inhabits a socket that’s already there, and it simply replaces a chip that is already on board – the endpoint needs memory, after all – so it adds minimal extra cost to the bill of materials.
Authenta may enable valuable differentiating security features
Security can usually – and should – pay for itself. It’s not just a checkoff feature. Security can help sell your product. IoT devices – and remember we speak of billions here – are often physically far-flung, unsupervised, and unguarded. You wouldn’t want your temperature sensors, smart meters, or ATMs to accept rogue firmware updates from hackers. The ability to verify that an update is legitimate – and block it if it isn’t – is a big advantage, because dispatching qualified technicians for updates to thousands of hard-to-access endpoints is out of the question. For example, Authenta can be integrated into a “verified-secure update” ecosystem, meaning it can be deployed with the ability to reject an update from an unauthorized or compromised source.
Our five-year outlook for TPMs and Authenta
We expect that TPMs will continue to prevail in the PC realm, where it has an established ecosystem built up since 2003. When it comes to IoT devices and endpoints, though, Authenta has a level playing field, and comes with features that make it more practical to securely create, deploy, and then manage (and update) IoT devices. Some supporting pieces need to appear around Authenta – tools to simplify solution development, and a robust management platform – but these are on the way. Applying a framework of usability, complexity, scalability and cost – we see Authenta as the winner in the IoT.
For information on how to architect and deploy TPM and Authenta-based solutions, contact TrustiPhi.
