TrustiPhi
Takes on and solves the toughest and most demanding security software and firmware challenges.
On time. At budget.
Take delays, cost, and risk out of your security development process.
Reduce development risks significantly.
Leapfrog product development delays and risks by entrusting this specialized work to TrustiPhi. We have a proven track record in delivering these specific types of projects.
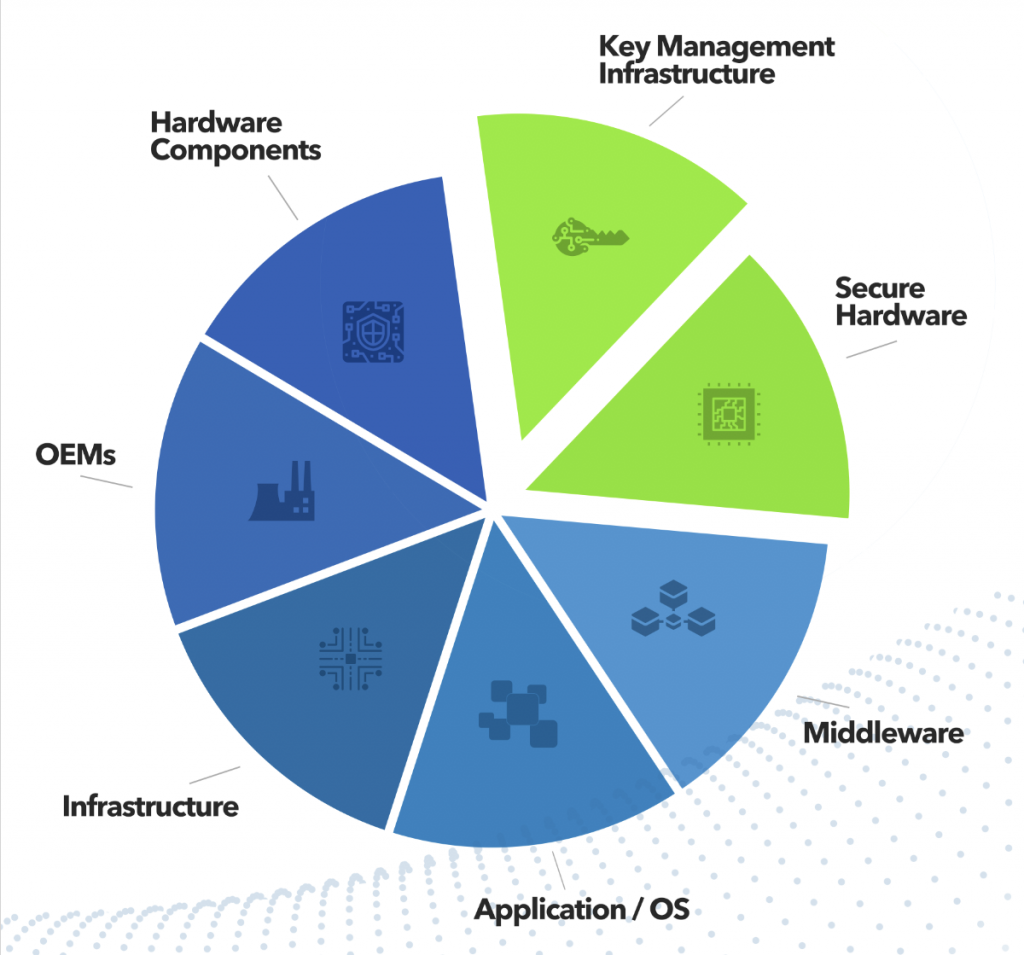
OEMs
TrustiPhi can work with you to enable the transformation of your device from a physical-only product to an ongoing revenue stream.
Software and Firmware Delivered on Time and at Budget
Authenta and Triathlon can work together to enable the transformation of your product from just a physical device to an ongoing revenue stream.
We have led the development efforts for security software and firmware that has shipped on hundreds of millions of systems worldwide, covering a variety of operating environments including Windows, Linux, RTOS, Android, iOS and non-OS environments. We can ensure that your solutions are built securely, on time and under budget. Our development services include the following:
SECURITY ARCHITECTURE IMPLEMENTATION
TrustiPhi not only designs security architectures. We also take them through to completion, working in collaboration with your staff as required.

RANGE OF OPERATING ENVIRONMENTS
Our clients often require versatility across OSs, and we cover Windows, Linux, RTOS, Android, iOS and non-OS environments.

MIDDLEWARE
DEVELOPMENT
Major technology providers engage TrustiPhi to deliver middleware at the platform, client, and server levels.

ON TIME.
AT BUDGET.
TrustiPhi is the best resources for strategizing and executing these specialized projects, which are often outside the core expertise of our clients’ in-house development groups.
TrustiPhi: Deep Expertise Supporting Clients
in Specific Areas
Middleware, security enablement of existing products, hardware-level security, and key management infrastructure
are primary focus areas where we assist our clients. From platform-control software and device drivers to the provisioning software, we provide the pieces of the overall security puzzle. Whether you make semiconductors, or products such as biometric sensors and smart cards, self-driving vehicles or voting machines, we can help.
Contact
TrustiPhi can discuss your security enablement requirements in a no-obligation meeting. If indicated, the next step for a new client may be a four- to six-week Security Review and Assessment. Please use our Contact page to reach out to us, or email us at info@trustiphi.com and we will respond to you promptly.
