TRUSTED PLATFORM MODULES:
Great Choice, But Maybe Not For Your IoT Products
By Ari Singer, CTO, TrustiPhi interviewed by Ives Brant
What determines whether you should build a security architecture around TPMs in 2023?
To answer that, we began by interviewing Ari Singer, who is CTO here at TrustiPhi and a long-time security architect with two decades in trusted computing. He has chaired both the Trusted Computing Group’s Trusted Platform Module (TPM) work group and the TPM Software Stack (TSS) working group and was a key contributor to the TPM 1.2 and 2.0 specifications. Read More
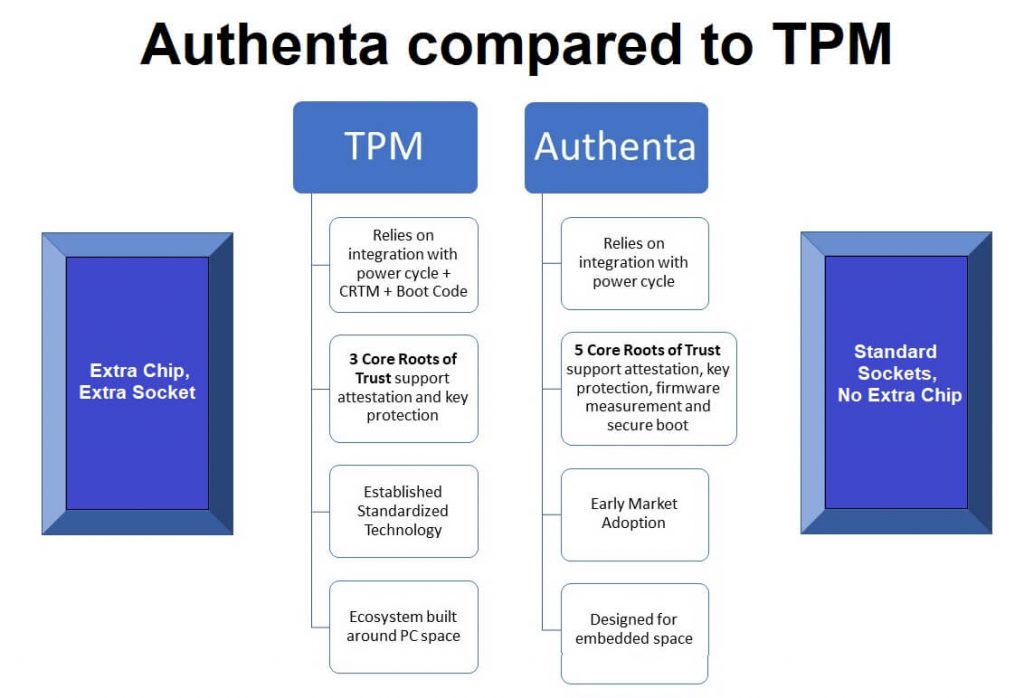
TPM Compared to Authenta for the IoT: Which is a Better Fit?
By Ari Singer, CTO, TrustiPhi and Ives Brant
Micron has integrated security technology into a flash memory chip, creating a two-in-one device that offers capabilities for attestation, secure boot, and other differentiating security capabilities, with no additional chips or changes to circuit boards. Get a clear picture of why Authenta has the potential to displace TPM as the hardware security technology of choice for IoT endpoint products, based on cost, ease of integration/design, ease of deployment, and security features. Learn about manufacturing advantages, and the “trust gain” that Authenta facilitates for IoT endpoint products. Read More
